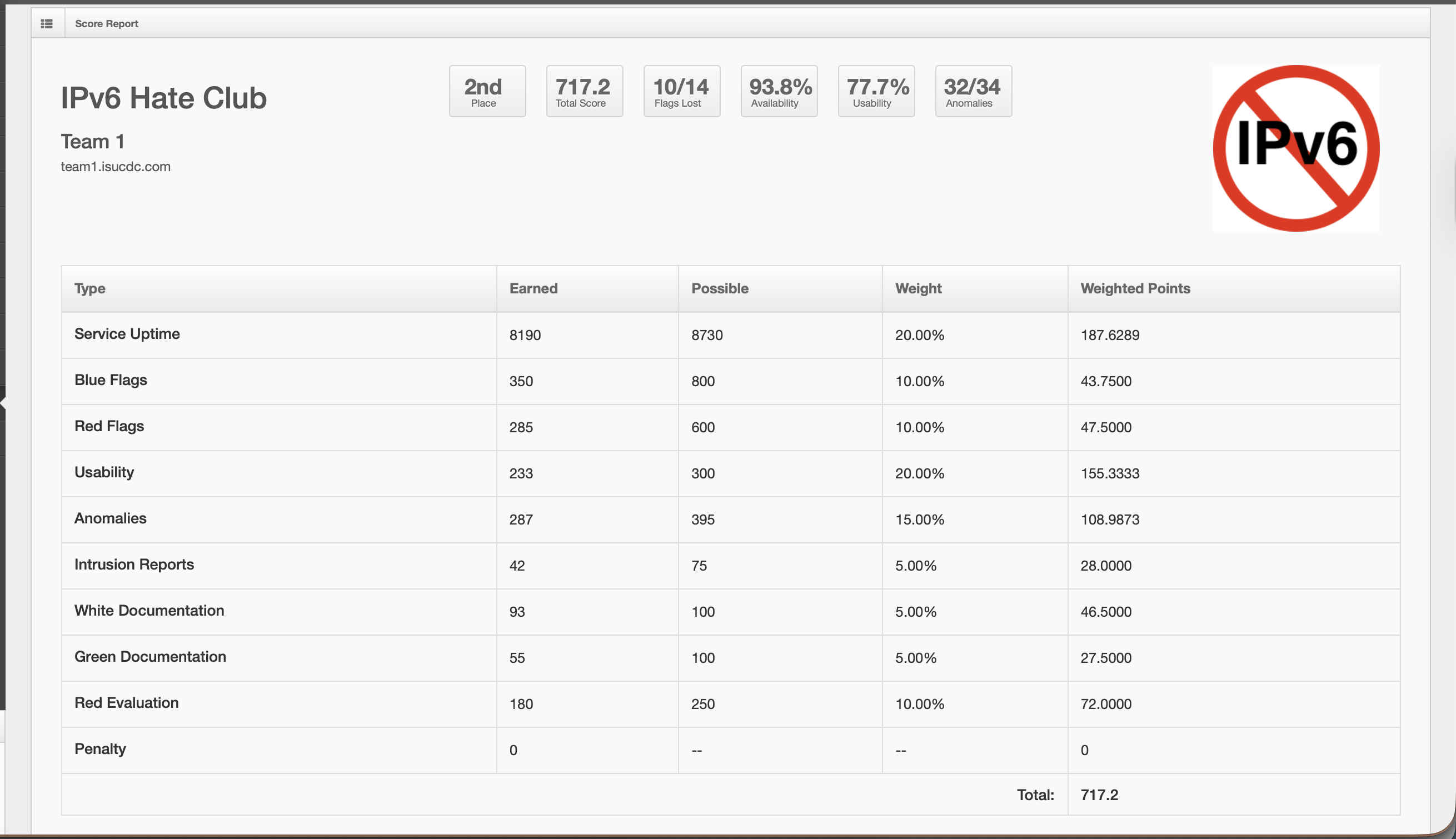
Competition Overview
Our Achievement: 2nd Place
2nd
Out of 10+ Teams
717.20
Final Score
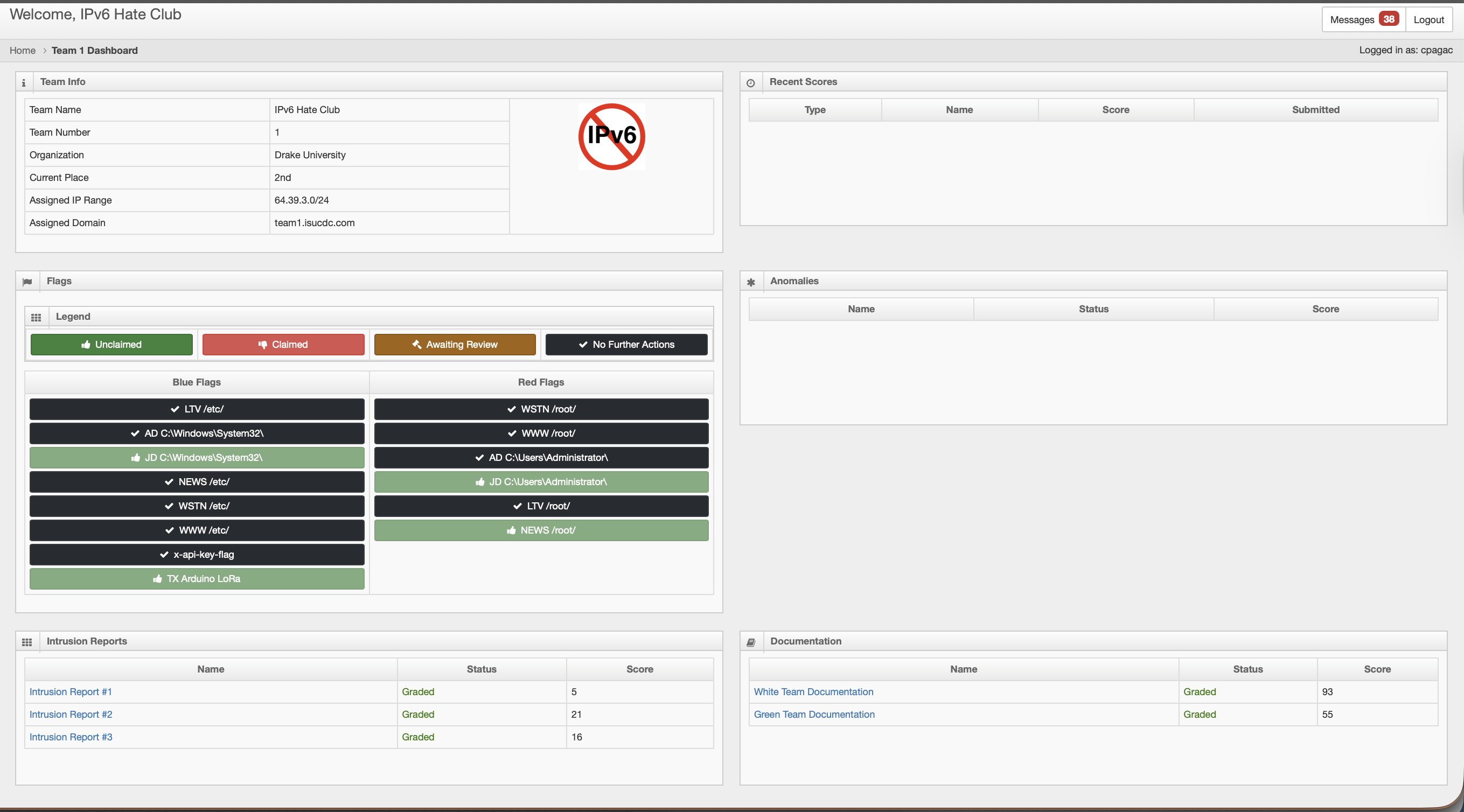
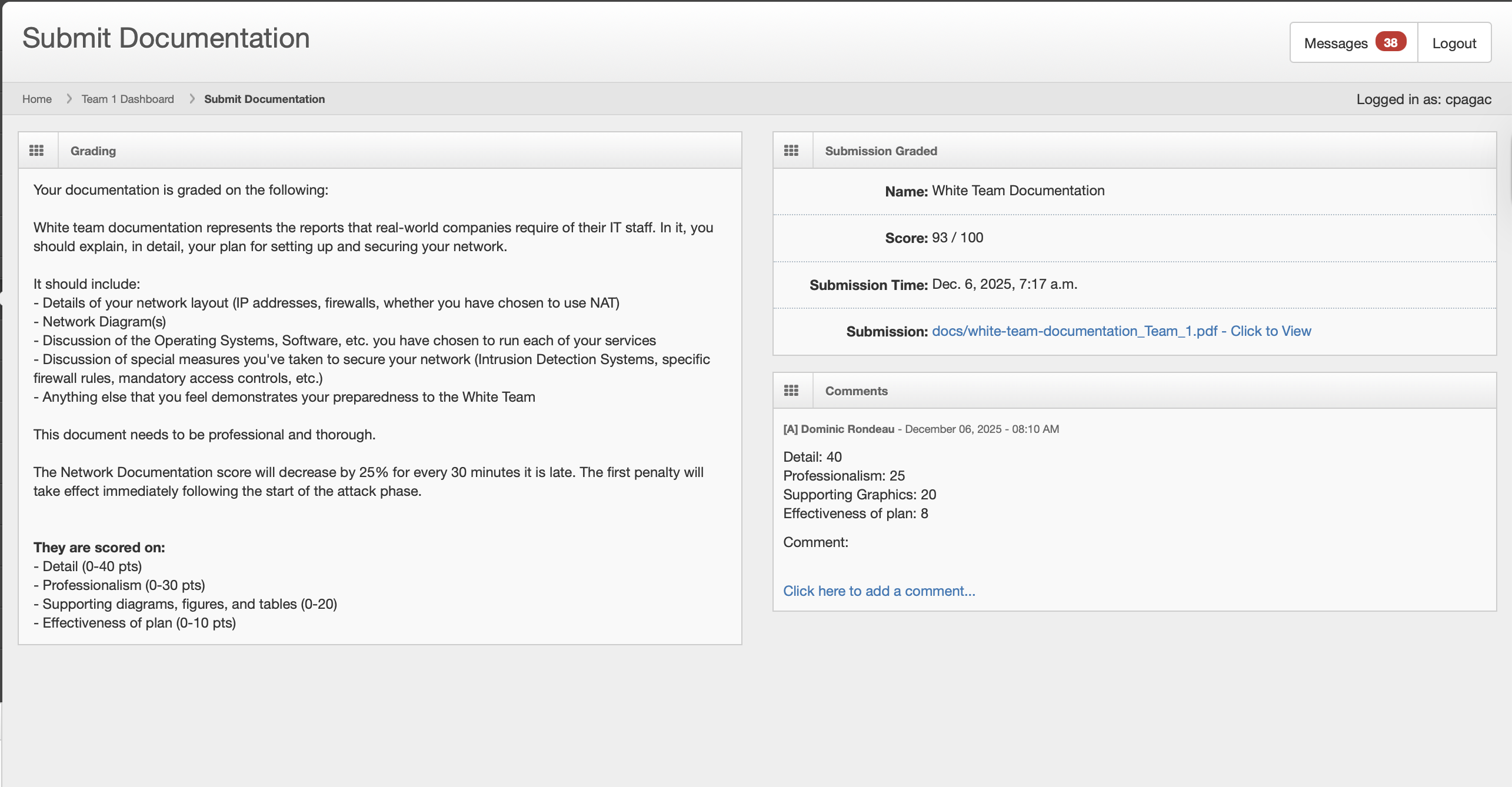
As the competition approached finals, I took the leadership role, designing and implementing our three-tier segmented network architecture, creating comprehensive white team documentation (93/100), and leading malware removal efforts across all systems. Our strategic network design isolated critical infrastructure from the UNTRUSTED network where Red Team had physical access, significantly limiting their lateral movement capabilities.
Network Architecture: Defense-in-Depth Design
I designed and implemented a three-tier network segmentation strategy that became the cornerstone of our defensive posture. This architecture enforced strict security boundaries through OPNsense firewall rules and isolated systems based on trust level and function.
Three-Tier Segmented Architecture
MGMT Network (10.10.10.0/24)
Purpose: Critical infrastructure and security monitoring
Systems: Active Directory (10.10.10.10), management systems
Security Policy:
- Full outbound access for management operations and updates
- Inbound access restricted to port 389 (LDAP) for authentication only
- IT Administrator RDP access from authorized systems
- All connections logged for security monitoring
Rationale: Compromise of AD would allow Red Team to pivot to all domain-joined machines, so we isolated it behind the strictest firewall rules.
INTERNAL Network (10.10.20.0/22)
Purpose: Production services and employee workstations
Systems: Web servers, News API, Journalist Desktop
Security Policy:
- Journalist Desktop can access web servers for article management
- Web servers can query News API for weather data
- DNS access (port 53) and internet via proxy (199.100.16.100:3128)
- Cannot initiate connections to MGMT or UNTRUSTED networks
Rationale: Prevents lateral movement if public-facing services are compromised. Attackers gaining access to web servers are blocked from reaching AD or management infrastructure.
UNTRUSTED Network (10.10.40.0/24)
Purpose: IoT devices with physical access vulnerability
Systems: Lobby TV, Weather Station
Security Policy (Most Restrictive):
- MGMT Network: COMPLETELY BLOCKED except port 389 (LDAP) to AD only
- INTERNAL Network: COMPLETELY BLOCKED except:
- Weather Station → News API (port 8080) for weather data
- Lobby TV → News API (port 8080) for broadcast stream
- Both systems → AD (port 389) for authentication
- DNS and proxy access allowed for legitimate functionality
- All outbound connections logged for C2 detection
Rationale: This is our most critical security control. Red Team had physical console access to Lobby TV via vCenter. If they compromised it, they could not pivot to AD or management systems, preventing the most dangerous attack path.
WAN Configuration & External Connectivity
Challenge: Gateway (64.39.3.254) was not on the same Layer 2 segment as our WAN IPs (all /32 host routes)
Solution:
- Enabled "Far Gateway" and "Upstream Gateway" options in OPNsense
- Configured 1:1 NAT mappings for external IPs to internal systems
- Routed all internet traffic through competition proxy (199.100.16.100:3128)
- Created WAN firewall rules allowing IScorE scorer (49.10.235.154) access to required ports
- Blocked all other unsolicited inbound traffic
Network Architecture Results
- Service Uptime: 93.8% availability across all systems
- Lateral Movement Prevention: Successfully prevented Red Team from pivoting between network segments
- Critical Infrastructure Protection: Active Directory remained secure throughout the competition
- Scoring: Network segmentation design contributed to our documentation and security posture scores
Application Security Remediations
We identified and fixed four high-severity vulnerabilities in the news website and weather backend applications that could have allowed complete system compromise.
CRITICAL SQL Injection (CWE-89)
Location: weather-backend/backend.go, POST /weather endpoint
Vulnerability: SQL queries constructed using string formatting with unsanitized user input, allowing arbitrary SQL command injection
Remediation: Replaced all string-formatted queries with parameterized SQL statements using placeholders. Database driver now properly escapes all user input.
Impact: Prevented potential data extraction, weather record modification, and database administrative operations
HIGH API Key Exposure (CWE-200)
Location: news-website/nuxt.config.ts and app/pages/weather.vue
Vulnerability: API key flag exposed in public runtime configuration, accessible via browser developer tools and JavaScript bundle inspection
Remediation: Moved API key to private server-side configuration. Created new server-side API route (/server/api/weather.ts) that handles backend authentication. Client now makes requests to our API route instead of directly to backend.
Impact: Protected sensitive credentials from client-side exposure while maintaining website functionality
HIGH Broken Access Control (CWE-862)
Location: weather-backend/backend.go, POST /weather endpoint
Vulnerability: Weather data upload endpoint had no authentication, allowing unauthorized users to inject arbitrary data into database
Remediation: Implemented API key validation on POST handler. Endpoint checks for valid x-api-key-flag header and rejects requests without proper authentication with 401 Unauthorized.
Impact: Prevented data corruption and manipulation of forecasts displayed on website and Lobby TV broadcast
HIGH Hardcoded Credentials (CWE-798)
Location: weather-backend/backend.go and news-website/server/db.ts
Vulnerability: Database credentials and API keys hardcoded in source code, creating exposure risk via version control, backups, and code repositories
Remediation: Refactored applications to read credentials from environment variables. Created systemd service override files at /etc/systemd/system/*.service.d/override.conf that securely store credentials using Environment directive.
Impact: Enabled credential rotation without code changes and eliminated version control exposure
Threat Hunting & Malware Removal
I led comprehensive threat hunting activities across all systems, identifying and removing numerous Red Team persistence mechanisms. Our systematic approach checked multiple layers where attackers commonly establish backdoors.
Windows Systems (AD, Journalist Desktop)
- Scheduled Tasks: Enumerated and removed suspicious tasks with random names, hidden attributes, and PowerShell execution from temporary directories
- WMI Event Subscriptions: Queried root\Subscription namespace for malicious __EventFilter, __EventConsumer, and __FilterToConsumerBinding objects
- Malicious Services: Audited Windows services for unusual names, services running from unusual directories, and obfuscated executables
- Backdoor Accounts: Discovered 'taco' account with administrator privileges. Encountered Active Directory corruption when attempting removal, requiring careful troubleshooting
Linux Systems (LTV, NEWS, WSTN, WWW)
- Malicious Cron Jobs: Found root cron job on LTV executing hidden .super_secret.sh script that created backdoor user 'richard' with blank password. Removed cron job and associated script. Similar exfiltration scripts found on other systems.
- Systemd Services:
- WWW: Discovered suspicious apt process (PID 168308) - actually chkrootkit installation masquerading as security tool
- NEWS copier.service: Service copying /etc/shadow to /tmp with world-readable permissions (777)
- NEWS network-broadcast.service: Broadcasting /etc/shadow over network using netcat to 255.255.255.255:1337
- LD_PRELOAD Backdoors: WSTN weather-station.service had LD_PRELOAD=/usr/lib/libssl.so.1.1, forcing malicious library loading. Removed environment variable from service configuration.
- PAM Configuration: Found 'nullok_secure' option in /etc/pam.d/common-auth on WWW and WSTN, allowing blank password authentication via SSH and local console
System Hardening Measures
Windows Hardening
CRITICAL Windows Update Service Disabled
Finding: Windows Update service completely disabled on Active Directory server (error 0x80070422)
Impact: Windows Server 2019 base installation vulnerable to:
- EternalBlue (MS17-010)
- BlueKeep (CVE-2019-0708)
- SMBGhost (CVE-2020-0796)
- Zerologon (CVE-2020-1472)
- PrintNightmare (CVE-2021-34527)
Remediation: Re-enabled Windows Update service and initiated installation of critical security patches
- Firewall Configuration: Enabled Windows Firewall on all profiles (Domain, Private, Public). Configured rules to block unnecessary inbound ports while allowing RDP and LDAP.
Linux Hardening
- SSH Hardening (All Systems): Disabled password authentication and empty passwords. Enabled public key authentication. Disabled TCP forwarding. Restricted TTY access.
- Security Updates Repository: Majority of Debian/Ubuntu systems had security repository commented out. Uncommented and ran apt update && apt upgrade to install all security patches.
- Password Hashing (NEWS): System using MD5 for password hashing (cryptographically broken). Reconfigured to use SHA-512 for stronger password protection.
- Package Manager Configuration: Configured apt to use competition proxy for downloads. Verified HTTPS usage for package repositories where possible.
Competition Results & Scoring Breakdown
2nd
Place (out of 10+ teams)
717.20
Total Score
93/100
White Team Documentation
93.8%
Service Availability
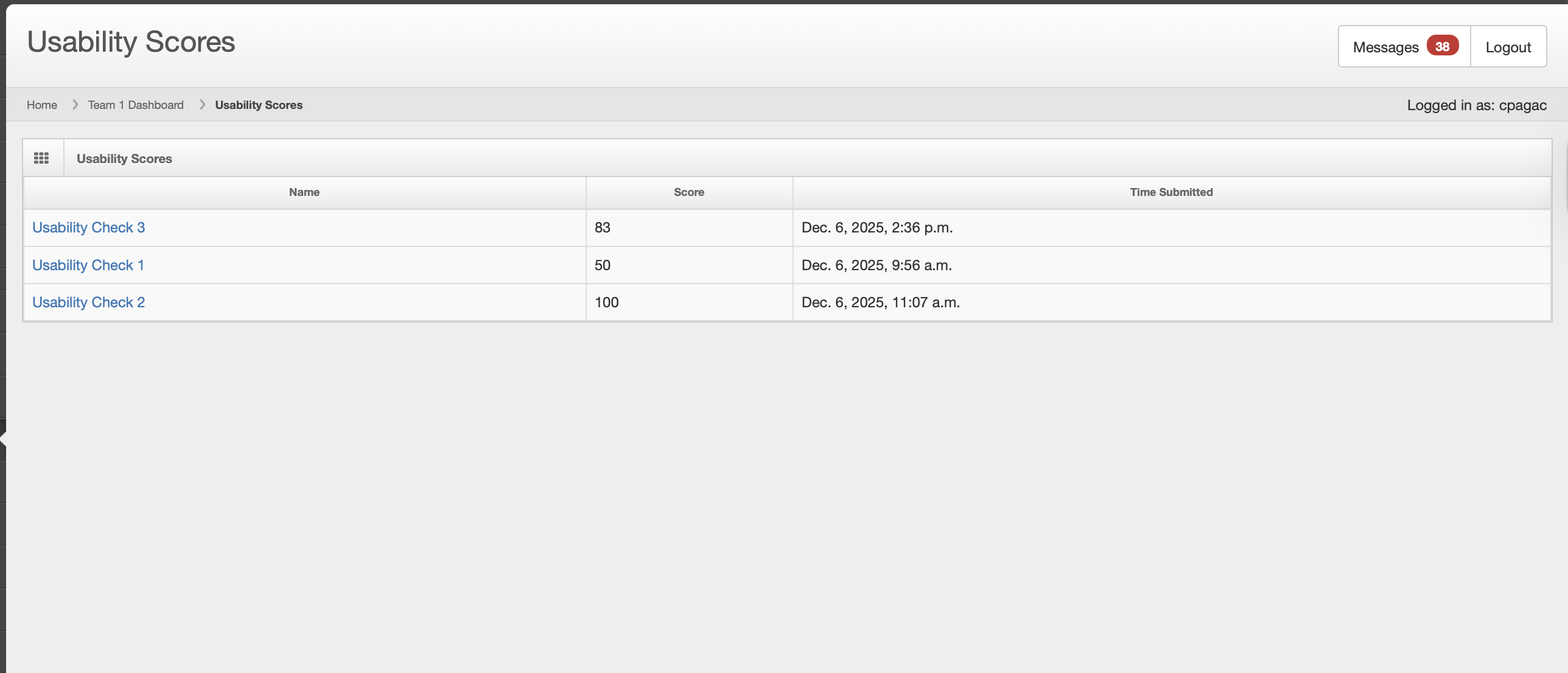
77.7%
Usability Score
8
Person Team
7
Systems Defended
8
Hours Competed
Competition Screenshots
.png)

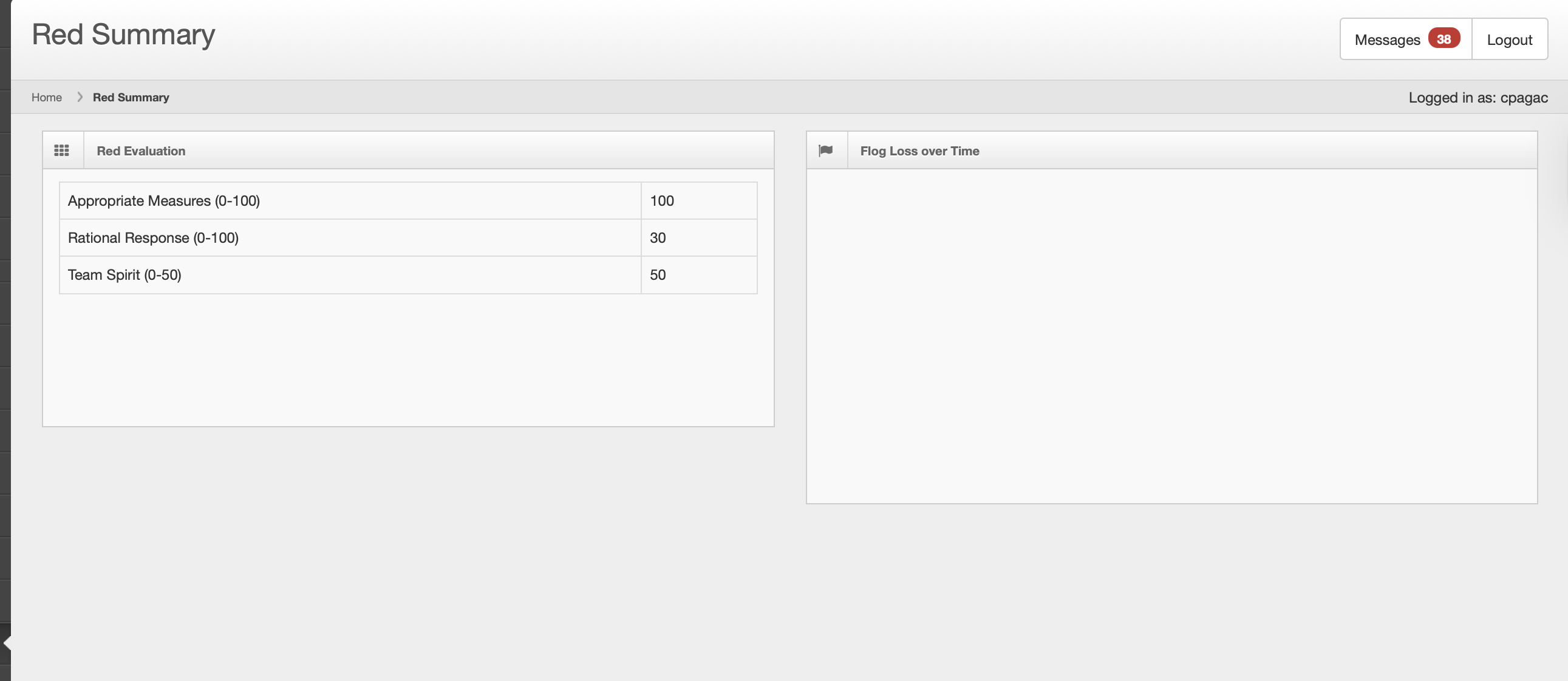
.png)
.png)
Key Technical Achievements
- Three-Tier Network Segmentation: Designed and implemented defense-in-depth architecture using OPNsense that isolated critical infrastructure and limited Red Team lateral movement
- Comprehensive Documentation: Created detailed white team documentation (93/100) covering network architecture, vulnerability remediation, threat hunting, and system hardening
- Application Security: Identified and fixed four high-severity vulnerabilities including SQL injection, API key exposure, broken access control, and hardcoded credentials
- Malware Eradication: Systematically hunted and removed persistence mechanisms across Windows and Linux systems including scheduled tasks, WMI subscriptions, malicious services, cron jobs, and LD_PRELOAD backdoors
- System Hardening: Implemented security patches, SSH hardening, firewall configuration, and secure password hashing across all systems
- Service Availability: Maintained 93.8% uptime across all required services while defending against active Red Team attacks
Lessons Learned
Leading the team through the C3 2025 CDC provided invaluable insights into enterprise network defense and incident response:
- Network Segmentation is Critical: Our three-tier architecture was our strongest defensive control. Even when Red Team compromised systems in the UNTRUSTED network, they couldn't pivot to AD or management infrastructure.
- Documentation Under Pressure: Creating comprehensive documentation during active defense operations requires careful organization. Using Notion for real-time tracking of vulnerabilities and remediation proved essential.
- Systematic Threat Hunting: Rather than reactive defense, proactive hunting for persistence mechanisms across multiple layers (scheduled tasks, services, cron jobs, PAM) was crucial for removing Red Team footholds.
- Application Security Matters: Infrastructure security is insufficient if applications have vulnerabilities. The SQL injection and API key exposure could have compromised our entire defense.
- Leadership During Crisis: Taking the lead as competition approached finals required balancing technical work with team coordination, prioritization, and maintaining morale under pressure.
- Configuration Management: Small misconfigurations (disabled Windows Update, commented security repositories) create massive vulnerabilities. Baseline hardening is essential before active defense begins.